 There’s a wicked string of malware on the Internet that locks users out of their browser and directs them to call a phone number. That phone number reaches hackers who have set up a subterfuge as an IT support company. If this happens to you, even if you are in the middle of something important, do not call the phone number.
There’s a wicked string of malware on the Internet that locks users out of their browser and directs them to call a phone number. That phone number reaches hackers who have set up a subterfuge as an IT support company. If this happens to you, even if you are in the middle of something important, do not call the phone number.
This particular piece of malware startles the user by blocking their progress within their web browser, suggesting them to contact a fake tech support hotline to “fix” their computer. It will show a screen that’s similar to the Windows fatal system error blue screen, along with a fake technical support message that pops up, informing the user of the “problem.” As you can see by the provided screenshot, this blue screen of death is deceptive because it’s only displayed within the browser, instead of taking up the entire screen like Microsoft’s real blue screen of death.
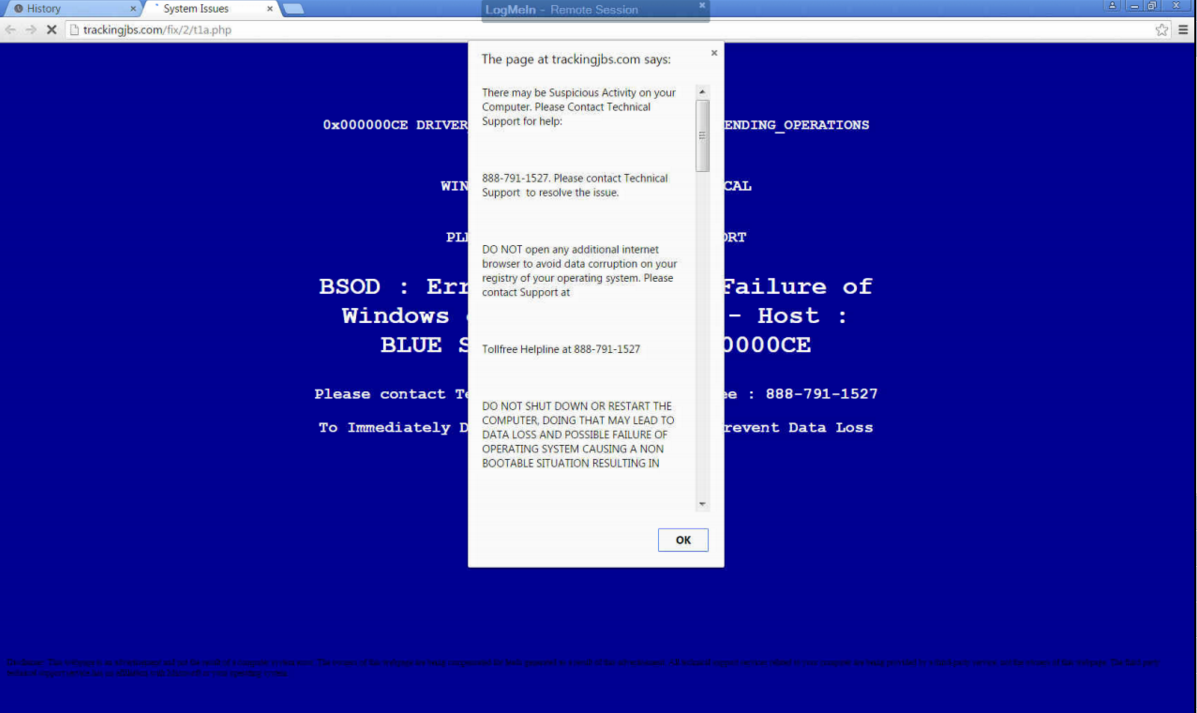
Whatever you do, DON’T CALL THE PROVIDED PHONE NUMBER. The blog Delete Malware explains: “If you call [the number] they won't actually remove adware from your computer. They will hijack your computer and steal all of your bank information and passwords. They are crooks, don't call them!”
Fortunately, this error isn’t as critical as what it seems. In fact, this is a common tactic of social engineering: make the problem seem much worse than it is, causing the victim to flip out and do something rash--like call the fake IT support phone number.
What then are you supposed to do? You can make the issue go away simply by closing the browser via task manager (Ctrl + Alt + Delete), or rebooting the PC. However, it’s still annoying to deal with because you’ll lose any unsaved data, along with any progress made to whatever project you’re working on. Plus, rebooting your system won’t technically solve the problem; the malware will still be embedded in your system, waiting for another chance to strike.
Therefore, to get down to the root of this problem, you’re going to want to isolate and properly delete the malicious file. For this level of real IT support, you’re going to want to call the trained professionals at Total Tech Care. We’ve got the tools needed to find and eliminate such threats, and even block them from hitting your system in the first place with a Unified Threat Management solution.
Lastly, we’d like to point out that the perpetrators of this hack are relying on the fact that the user doesn't know who to call for IT support in a crisis situation. It’s reasons like this why you and your staff need to be familiar with who to call in an emergency IT situation, like Total Tech Care at 866-348-2602. When it comes to taking care of IT issues, we’re the real deal, and we take offense that hackers these days are posing as trustworthy IT technicians in order to get at a user's personal data. It’s an unsettling trend that will only be brought down by companies being vigilant about their network security.
To that end, Total Tech Care can help. Call us today to find out how we can protect you from the worst of the web.




