 Modern ransomware is exceptionally dangerous, even by malware standards. Ransomware is capable of locking down important files on a victim’s computer, displaying a massive threat to both business professionals and their networks, as well as the average PC user. While other types of ransomware like CryptoLocker and CryptoWall are somewhat manageable, a new variant called CryptoJoker makes it borderline impossible to recover your files.
Modern ransomware is exceptionally dangerous, even by malware standards. Ransomware is capable of locking down important files on a victim’s computer, displaying a massive threat to both business professionals and their networks, as well as the average PC user. While other types of ransomware like CryptoLocker and CryptoWall are somewhat manageable, a new variant called CryptoJoker makes it borderline impossible to recover your files.
Similar to other types of ransomware, CryptoJoker locks down the victim’s files through encryption, and will only decrypt the files once the ransom has been paid to the hacker in full. The ransom is generally paid in Bitcoin to preserve the anonymity of the crook holding your data. The idea is to strike fear into the hearts of their victims, and play on this fear to extort money from them for the safe return of their files. Ransomware like CryptoJoker is typically spread through email phishing scams, but in this case, CryptoJoker infects users through a phony PDF file.
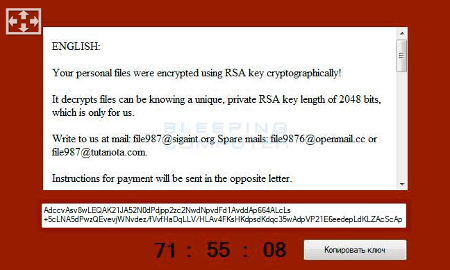
After the user has been infected by CryptoJoker and the ransomware has installed, it will scan all drives connected to the infected device. This includes all network drives connected to it. CryptoJoker then proceeds to encrypt specific file extensions, most of which are absolutely critical to your business’s continued functionality:
- .txt
- .doc
- .docx
- .xls
- .xlsx
- .ppt
- .pptx
- .odt
- .jpg
- .png
- .csv
- .sql
- .mdb
- .sln
- .php
- .asp
- .aspx
- .html
- .xml
- .psd
- .java
- .jpeg
- .pptm
- .pptx
- .xlsb
- .xlsm
- .db
- .docm
- .sql
CryptoJoker isn’t widely distributed, so you can breathe easy knowing that you probably won’t run into it anytime soon. Still, what would happen if you were to get infected? CryptoJoker isn’t something to laugh at; the quality of its encryption is military-grade AES-256 encryption, which makes it impossible, in most cases, to crack. Users are often left with no choice but to pay the ransom to CryptoJoker’s developers. Thus, the key to preventing ransomware from destroying your data is to prevent it from infiltrating your computer in the first place. If you do get infected by CryptoJoker, you better hope that you have a data backup solution that’s ready to work overtime.
If you don’t have a backup of your data available, you’re out of luck. Even in the worst case, though, you shouldn’t be paying criminals for the decryption key if you can help it. Just because they claim that they’ll give you the key in exchange for payment, doesn’t mean that they’ll stick to their word. There’s nothing stopping them from taking your money and leaving you high and dry. Other ransomware is notorious for taking payments and not decrypting your files, so it’s safe to say that you shouldn’t trust CryptoJoker either.
If you aren’t sure whether or not your security solution has what it takes to protect your organization from CryptoJoker, Total Tech Care can help. We can arm your business with solutions that are designed to protect your systems from CryptoJoker and other ransomware before you get infected. In most cases, this is the best thing we can do for you; recovering your encrypted files is often borderline impossible.
For more information about cybersecurity best practices and how to protect your organization from ransomware, give Total Tech Care a call at 866-348-2602.




