 Let’s say that you get new equipment and software for your company’s network, expecting to see a boost in performance. When everything is tested, you see no change in performance, which understandably bums you out. In a situation like this, your network is likely bottlenecking.
Let’s say that you get new equipment and software for your company’s network, expecting to see a boost in performance. When everything is tested, you see no change in performance, which understandably bums you out. In a situation like this, your network is likely bottlenecking.
Bottlenecking gets its name from the design of a bottle (think wine bottle) where the neck narrows to allow for a smaller amount of fluid to pour from the bottle’s opening than would come out if the opening was just as large as the base, like with a pickle jar. Techquickie defines bottlenecking (also known as a choke point) as, “Holding back the performance that could otherwise be achieved.”
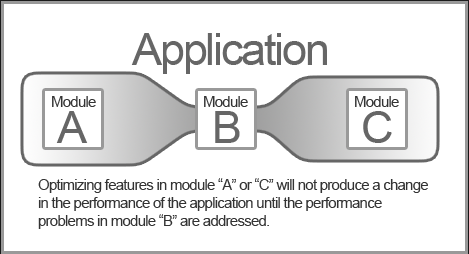 When you're experiencing a performance-hampering bottlenecking situation with your company’s network, the challenge is to locate the source of the problem and resolve the issue so that the rest of your network can reach its full potential. This is typically done by upgrading whatever is causing the choke point so that it meets the same performance standards as other components that make up the network.
When you're experiencing a performance-hampering bottlenecking situation with your company’s network, the challenge is to locate the source of the problem and resolve the issue so that the rest of your network can reach its full potential. This is typically done by upgrading whatever is causing the choke point so that it meets the same performance standards as other components that make up the network.
A classic example of this is when a PC user upgrades one component of their machine, like a video card, hoping to see an overall improvement in performance, but they end up experiencing minimal-to-no-boost because other factors that affect performance (like CPU and RAM) are old and already maxed out. This is a common occurrence with workstations and home computers, and as the technology becomes more complex with more computers and components in the mix, there’s a higher chance of there being bottleneck issues.
Therefore, when you’re dealing with something as complex as a computer network, with multiple workstations, servers, and NAS devices, you’ve substantially increased the risk of experiencing a bottleneck. For example, even if you’re working with top-of-the-line computers and powerful server units, your network routers can be old and outdated, which will prevent your powerful equipment from reaching its full potential; and, vis–à–vis, hold your company back from fully realizing its competitive goals.
Locating the exact cause of a network bottleneck requires a thorough knowledge of every component, which is why calling professionals to troubleshoot your network’s performance issues is often the smartest move. Otherwise, it would be quite easy to place the blame for performance issues on the wrong piece of equipment, replace said piece of equipment, and then, after investing all of that time and effort into the wrong fix, have to go back and try it again.
Total Tech Care has the tools it takes to run diagnostics on your company’s network to quickly determine what the exact cause of your bottleneck is. Depending on what the issue is, we may even be able to determine the cause of your bottleneck with our remote tools. This remote approach will save a technician a trip to your office, and save you money on your IT bill.
To schedule Total Tech Care to take a look at your network so we can unclog the log jam that’s holding your business back, give us a call at 866-348-2602.




