 If you’re one of those people who are always checking their inbox, you might be dealing with a lot of unnecessary stress in the workplace. A study has linked constantly checking your email inbox to higher stress levels. While this might not come off as much of a surprise, researchers at the University of British Columbia have managed to put a number to the maximum amount of times you should be checking your email to minimize stress.
If you’re one of those people who are always checking their inbox, you might be dealing with a lot of unnecessary stress in the workplace. A study has linked constantly checking your email inbox to higher stress levels. While this might not come off as much of a surprise, researchers at the University of British Columbia have managed to put a number to the maximum amount of times you should be checking your email to minimize stress.
According to their test, the maximum number of times you should be checking your email for minimum stress levels is three times. The study involved 124 adult workers over a seven-day testing period, in which they were only able to check their email three times a day. Then, the following week, workers were encouraged to check their email inbox whenever they got a spare moment. This is generally how most workers are in the office. At the end of each workday, the test subjects were asked to fill out a short questionnaire about their current stress levels.
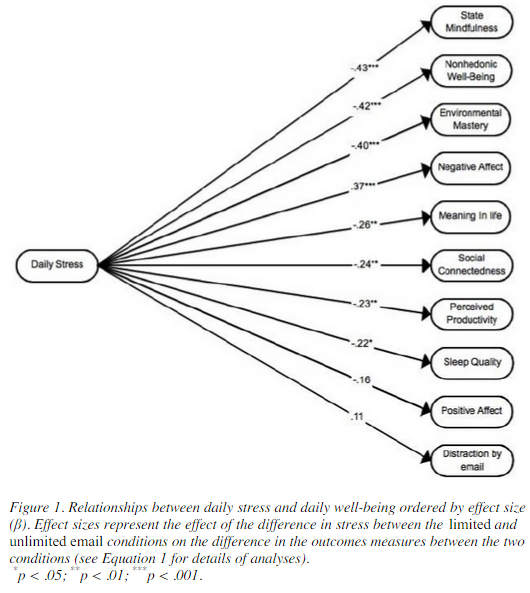
When encouraged to check their email as often as possible, the average worker checked their email 15 times throughout the day. Unsurprisingly, the primary reason checking email is so stressful for the average worker is that they have to constantly shift from urgent work tasks, to checking email, to personal matters. It’s no wonder that workers get so stressed out, especially when some email recipients expect immediate answers. This might be why, at first, workers were somewhat hesitant to only respond to their emails three times a day. In fact, according to Mashable, 92 percent of workers in the United States use email for inter-office communication, and as many as 183 billion emails are sent out on a daily basis. This root of email stress lies in the need to stay connected at the workplace.
Ideally, according to the study, workers should only have about three periods of email correspondence throughout the workday. To accomplish this, set aside a block of time at the beginning, middle, and end of your day to respond to emails that demand your attention. You might notice a significant decrease in stress. Unfortunately, not all business professionals can manage this with their busy schedules. If this is the case with you, here are some tips which might help you understand that your email inbox isn’t as important as it seems:
- If it’s especially important, you’ll receive a phone call or instant message about the issue at hand. If you have something urgent which needs to get done, try making a phone call yourself, and save the time you might have wasted drafting the perfect email message.
- You can’t afford to continuously respond to emails all day long. Continuously halting more important tasks isn’t ideal for productivity, concentration, or quality of work.
- If it’s not marked as important, it’s probably not important.
If you can manage to move away from checking your email constantly, great. However, you still want to make sure that the messages you are receiving are real, legitimate messages. Spam is a problem which makes checking email slightly more stressful due to its potentially-disastrous nature and its reputation for being a time-waster. With an enterprise-level spam blocking solution from Total Tech Care, you can mitigate the spam received during the workday and free up more time for important tasks.
If you’re ready to stop wasting time and dealing with unnecessary stress concerning your email inbox, give Total Tech Care a call at 866-348-2602. We’ll work with you to manage your technology in the most efficient way possible.




