 As the world pushes toward a more mobile era, so too does the workplace embrace Bring Your Own Device (BYOD) with open arms. As such, workers will need some type of network connection in order to access mission-critical corporate data. Therefore, if they can’t connect to a WiFi network, they’ll default to their cell provider’s mobile data plan.
As the world pushes toward a more mobile era, so too does the workplace embrace Bring Your Own Device (BYOD) with open arms. As such, workers will need some type of network connection in order to access mission-critical corporate data. Therefore, if they can’t connect to a WiFi network, they’ll default to their cell provider’s mobile data plan.
Unfortunately, too much strain put on this asset can quickly drain, or even surpass, your maximum monthly data expenditure. Therefore, reducing your mobile data usage can be a great way to cut down on your expenses and potentially improve battery life. Here are four ways to get started.
 Monitor Your Current Data Usage
Monitor Your Current Data Usage
Before jumping too deep into how to limit your data usage, you first need to identify whether or not you’re using too much data. Chances are that if you aren’t having difficulty staying within your monthly data usage, you don’t need to make many changes to the way you use your device. However, if you find yourself constantly violating your maximum data limit, you’ll know you need to change the way you’re using your device.
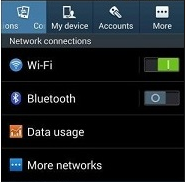
Use WiFi Whenever Possible
A simple way to lower your use of mobile data is to stop using it whenever WiFi is available. Rather than using up your mobile data plan, you can simply take advantage of any wireless networks in range. While this is convenient, you don’t want to connect to any sketchy wireless hotspots in your vicinity. There’s always the chance that a network can be littered with threats. Therefore, the best way to keep your device secure is to only access connections with passwords and encryption, and to make sure your autoconnect feature is turned off.
Limit Your Media Consumption While Mobile
Though it makes life infinitely more enjoyable to stream music and video entertainment on the go, it can also be putting an enormous strain on your mobile data plan. Instead of streaming music through your 3G or 4G connection, try playing music stored locally on your device. This can prevent your device from consuming too much data too quickly.
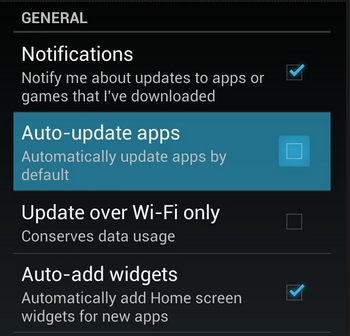
Limit Which Apps Update in the Background
Unless you’ve explicitly configured your device otherwise, your applications will automatically update in the background while you’re going about your daily routine. Unfortunately, this can eat up a ton of data. To prevent this, you can set your device to update automatically when connected to WiFi, or to manually perform the updates yourself.
If you find that even these four tips can’t stem the flow of your data problem, it might be time to cave in and get an upgrade. This should only be considered as a last resort, since it can help you avoid the overage fees associated with monthly data plans. All it takes is a little awareness of how much data you’re truly using in order to self-police yourself into staying within the confines of your monthly data plan.




