Heavy users of Google Drive may experience the issue of running low on storage space. The easiest way to resolve this problem is to give Google money and upgrade your account. Before taking this step, there are a few tricks you can do to free up Google Drive space by locating and getting rid of unneeded files.
Heavy users of Google Drive may experience the issue of running low on storage space. The easiest way to resolve this problem is to give Google money and upgrade your account. Before taking this step, there are a few tricks you can do to free up Google Drive space by locating and getting rid of unneeded files.
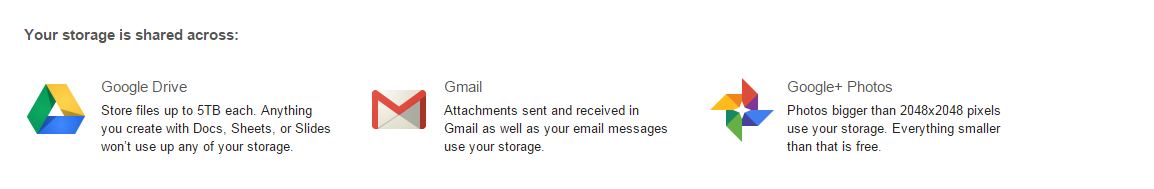
One reason why it’s possible to miscalculate how much storage space is being used by your Google Drive account is due to the fact that the 15GB every Google user gets isn’t a full 15GB of storage space. Of this 15GB of Drive space, Google allots this space for its various services, like Gmail and Google+.
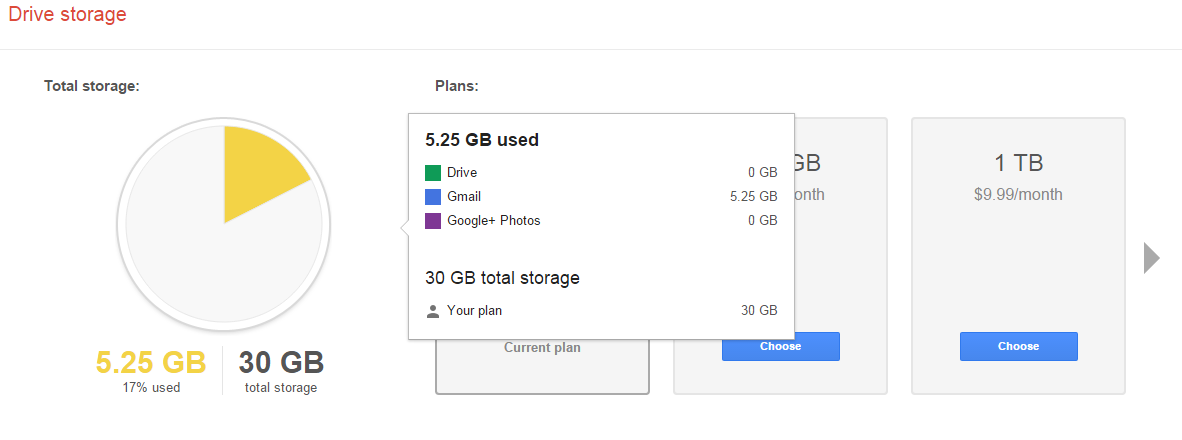
To find out exactly what’s taking up space in your Drive account, go to your Drive’s storage page. This will provide you with a handy-dandy pie chart that lays everything out for you.
This chart displays how much storage space is being used and what the space is being used for. From here, you can spot the unneeded files that are taking up space. For example, the email attachments in Gmail end up in your Drive account, as well as all of your photos from Google+. You might want to sift through your Drive and delete these files if you don’t need them.
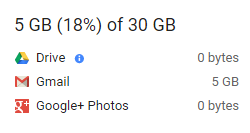
On your Drive storage page, you will find below the graph a section displaying specific information about space usage. Be sure to reference this if you’re on the hunt to free up space.
As is the nature of computer data, you will notice that the bulk of your space is likely to be taken up by media-rich files, like photos, music, and videos. Users of Google Apps that take advantage of Docs, Sheets, Slides, etc., will notice that these files don’t take up nearly the amount of space as does the large media files.
Therefore, if you’re looking to purge your Drive account and free up the most space possible, it’s best practice to start deleting the largest files first. To figure this out, go to the lower left-hand side of the screen in Drive, right above the link that says “Buy more storage.” From here, you’ll see your current storage use. Hover over it and a box will appear with more specific numbers. Click Drive.
This sorts your files by Quota used. From here, you can most efficiently manage your files.
Keep in mind that if you delete email files all willy-nilly, you may end up deleting something important that you’ll regret. Therefore, it’s best practice to archive your emails with a secure email solution. Total Tech Care can provide this for you.
Got an Android device? If your device is linked to your Google Drive, then it may be adding some rather large files to your storage, especially if you use your Drive account to back up your Android device’s photos and videos. One way that you take control of this is to adjust the size of pictures stored from your device to Drive. To do this, go to Settings > Auto Backup > Photo Size, then select Standard size. Keep in mind that there may be instances when you don’t want Google to change the size of your images, so keep this file path in mind.
By following these steps, you will free up space on your Google Drive account and not have to upgrade. To learn more data storage tips and best practices, call Total Tech Care at 866-348-2602.