 What’s the best way to share files between your different personal devices and computers? It turns out that you can share files over your home’s network, and you don’t have to be an IT technician to do it.
What’s the best way to share files between your different personal devices and computers? It turns out that you can share files over your home’s network, and you don’t have to be an IT technician to do it.
To be sure, there are many different ways to share files between your different devices. You can send an email from one device to another. You can upload the file to a cloud data storage service. You can even use an external data storage device like a USB thumb drive. While all of these methods will do the trick, some are more inconvenient than others (like using a thumb drive), while others (like the first two examples) require an Internet connection and reliance on a third party.
Instead, you might be surprised to learn that you can just as easily (if not more easily) move files over your home network to your different devices by dragging and dropping what you need to a shared folder. This functions similarly to how your computer network at the office is set up with its server units and multiple workstations. However, you don’t need a home server unit to share files across your different devices at home. Instead, if you’ve got two computers connected via your home’s Internet router, then you’re all set to easily share files between the two machines.
Share Files Using My Network Places
To do this, open My Network Places, locate a file associated with the computer that you want to share files with (designated by the PC’s assigned name), and then drag and drop your content into the shared file. To access the shared content with the computer that you just shared it with, locate My Network Places on your other computer and open the file that corresponds with the actions you just took.
Or Create a Windows Homegroup
If for some reason you’re unable to share the files you need between your two computers using My Network Places, then you can set up a Windows Homegroup. To do this, type “homegroup” in the Windows search box and then hit Enter. From here, Windows will let you know if there are any homegroups on your network. If it can’t find one, click Create a homegroup.
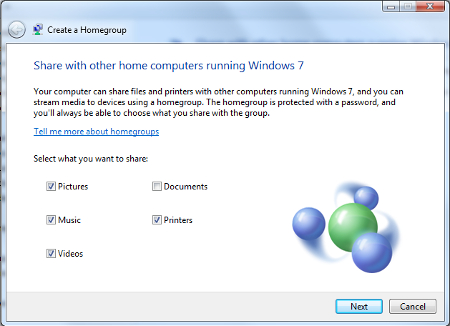
Next, select what kind of content and devices that you want to share in this homegroup and then select Next.
Windows will now generate a password that you will want to use for other computers to access the newly created homegroup. Be sure to record and share this in a secure manner if you’re adding multiple users to the homegroup.
Lastly, using the other computer on your home network, search for “homegroup” in the Windows search bar. This should bring up a dialogue box letting you know that a new homegroup has been added to your network. It will display the name of the computer you’ve originally used to create the homegroup. Now, just click Next > Enter the password > click Next again > and you’ll have both of your computers set up on the homegroup for easy file sharing.
If you need professional assistance with any of your computer networking needs, give Total Tech Care a call at 866-348-2602.




